Arm Confidential Compute Architecture
Our vision for the Arm Confidential Compute Architecture (CCA) is to protect all data and code wherever computing happens – unlocking the power and potential of data and AI. Arm CCA is part of a series of hardware and software architecture innovations that enhances Arm support for confidential computing. Arm CCA is a key component of the Armv9-A architecture achieving our goal of delivering the benefits of confidential computing to every industry sector.
Confidential Computing: A New Model of Trust on the Arm Architecture
Computing has become a distributed utility where computing sessions can run on any platform that meets the required security policy, making the ability to trust the computing utility infrastructure crucial to ensure confidence in the security and privacy of information. This model is a prime target for cybercriminals, intent on stealing data and code.
Confidential compute is a broad term for technologies that reduce the need to trust a computing infrastructure, such as the need for processes to trust operating system (OS) kernels and the need for virtual machines to trust hypervisors. While threats span all industry sectors, the Arm architecture is unique in the breadth of form factors and markets where it is used and our partners are actively innovating and delivering confidential computing using existing Armv8-A devices.
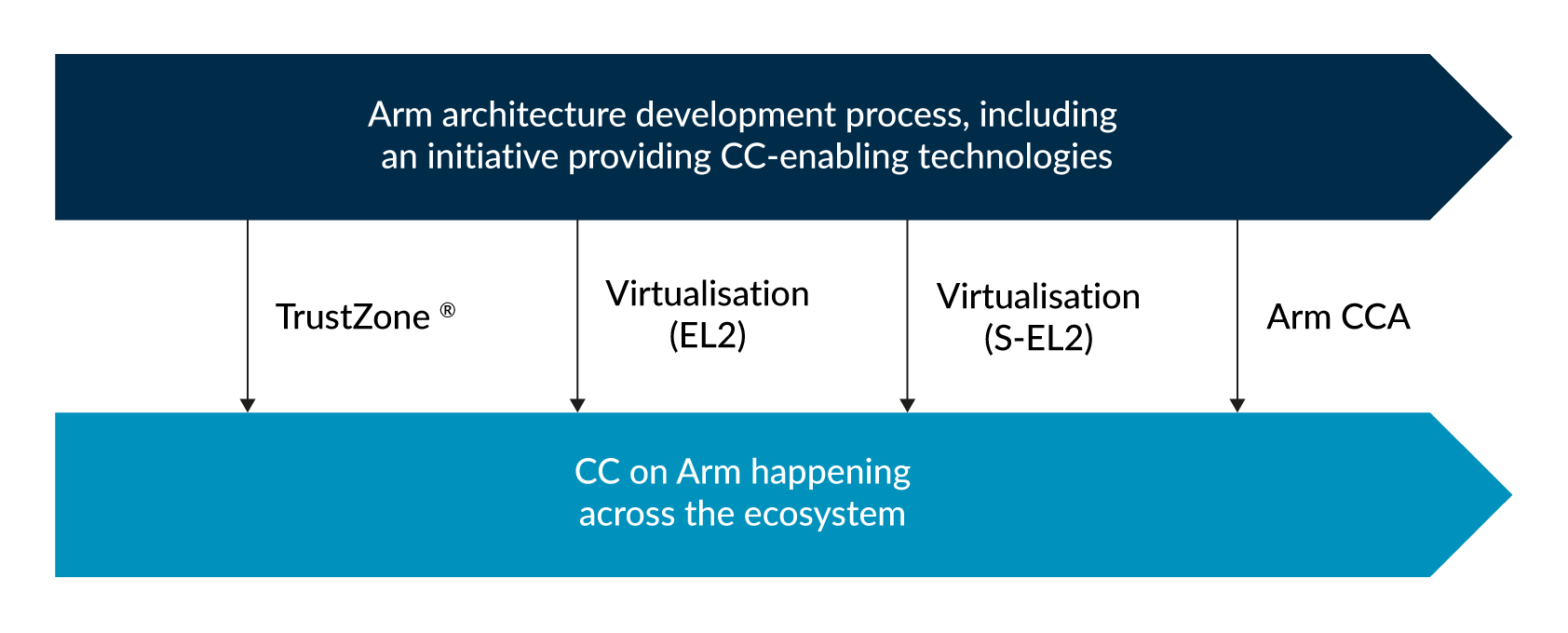
Arm CCA builds on the strong security foundations of TrustZone and introduces the concept of dynamically created Realms to be both evolutionary and revolutionary.
Components of Arm CCA
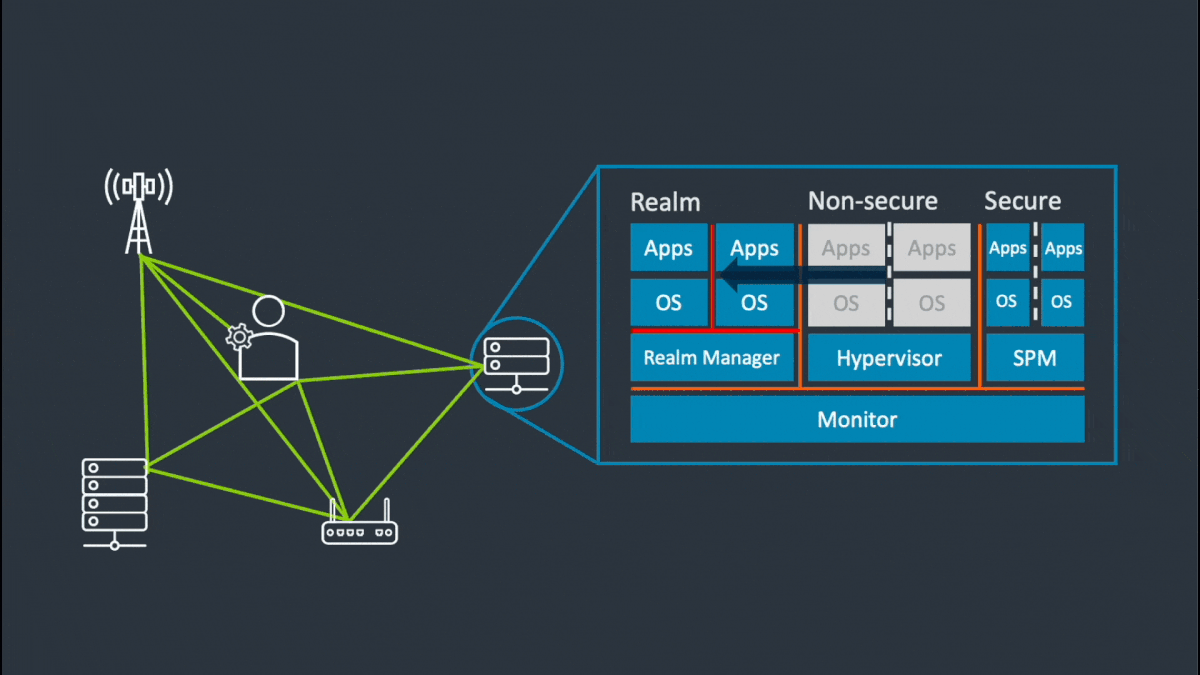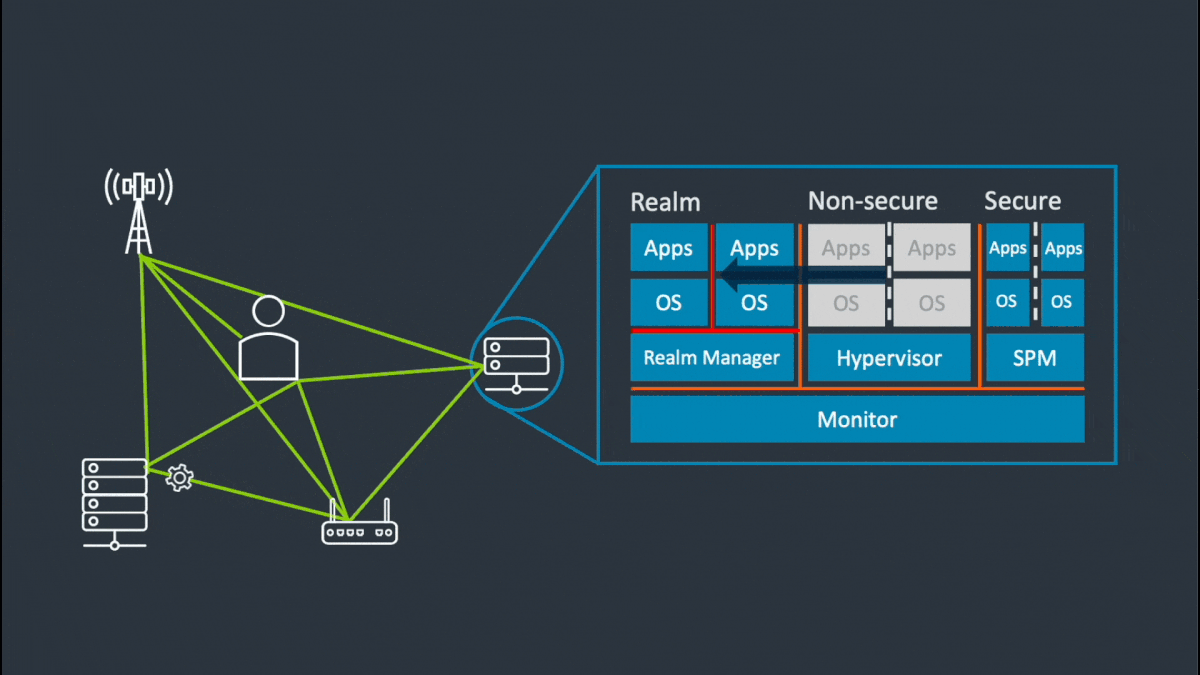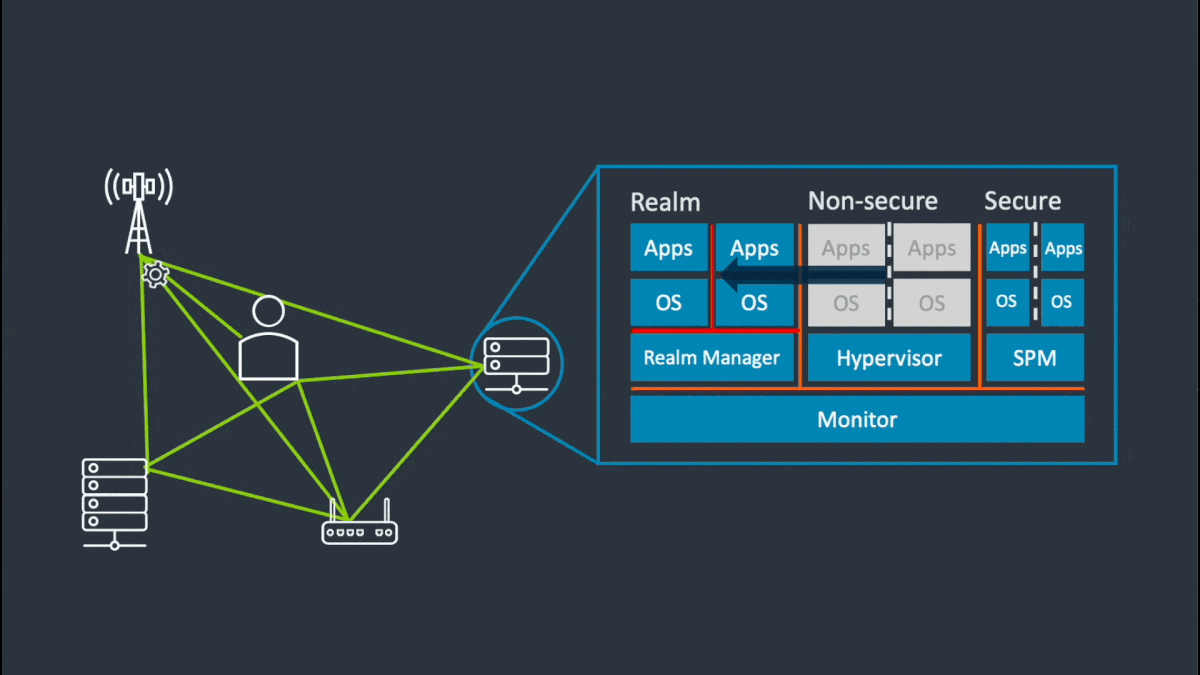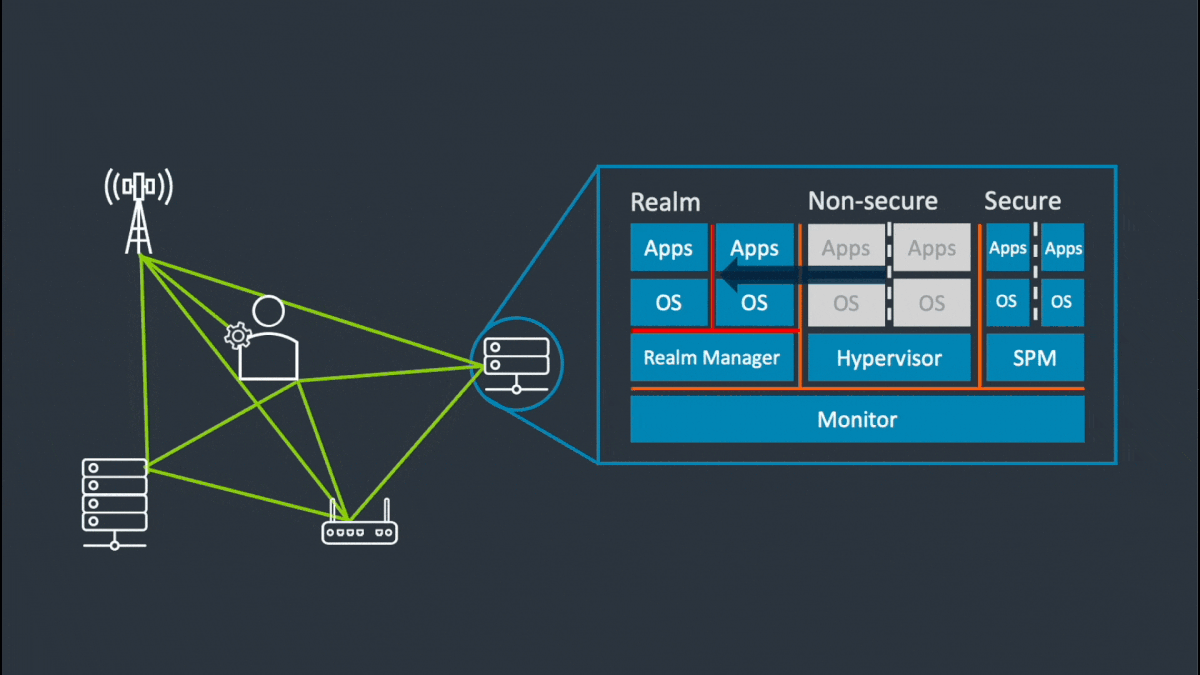
The diagram shows components of the Arm Confidential Compute Architecture.
Click the hotspots to see the details.
Realm Management Extension for Access Control
At the hardware level, the new Realm Management Extension (RME) protects all data and code, even while it’s being used, enabling improved control of who can access data and algorithms. This is the technology that will unlock the true power and potential of data sharing and AI.
RME supports a new type of attestable isolation environment called a Realm. Realms extend confidential compute to all software developers, democratizing secure computing. It also moves providers further from a position of will not access customer data to cannot access customer data. The RME reduces the volume of software that must be trusted, the attack surface for hackers, and the opportunity for customer data breaches.
Realms provide additional execution environments to ordinary programs for the secure processing of confidential data. Realms are isolated from the existing Normal and Secure Worlds that we have today in TrustZone. The security policy of a Realm is configured using a small amount of trusted and attestable software. This software is inherently separated from the Normal-World OS and hypervisor, and from any Secure-World hypervisor and trusted OS.
Securely Run All Applications
Arm CCA security enables applications to run in a secure way and therefore be accepted, trusted and deployed. It leverages the Arm standardization that enables interoperability and portability ensuring ecosystem success.
Benefits of Arm CCA
Fully secures third-party data and code for its owner so that it is not accessible by platform owners.
Ensures minimal impact on existing trusted applications as Realms can work alongside TrustZone.
Applies to any market or form factor that uses microprocessors.
Democratizes secure computing for all developers, and increases scalability, not just those working closely with silicon vendors and device OEMs.
Supports seamless portability across the ecosystem of Arm devices as Realms can be used at the virtual machine level.
Allows Realm owners to verify and prove the integrity of the underlying platform and Realm configuration with native support for attestation.
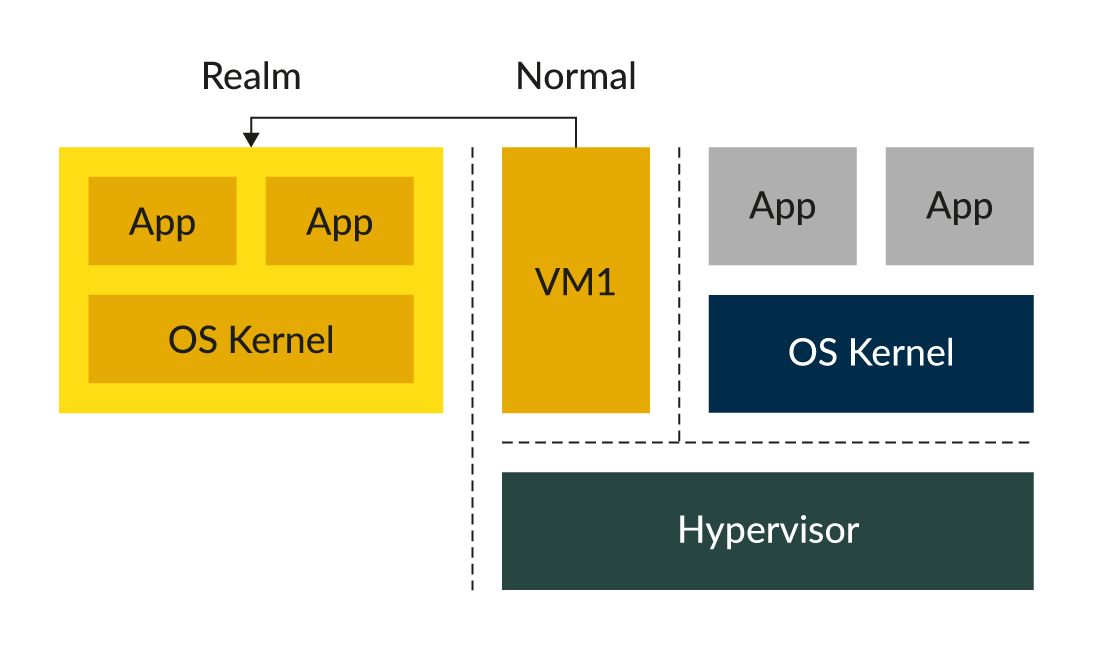
How Realms Execute in a Protected Memory Space
The Realm Management Extension (RME) supports a new class of attestable isolation environment called a Realm. Realms are isolated from the existing Normal and Secure Worlds that we have today in TrustZone.
As shown in the diagram below, RME protects mainstream computing workloads, such as virtual machines or containers from privileged software and hardware agents including the hypervisor, the Normal World kernel and even TrustZone applications.
Re-Evaluate Trust Relationships
Today, computing is a distributed utility where computing sessions can be run on any platform that meets the required security policy. The ability to trust this computing utility infrastructure is a crucial element in ensuring that people are confident about the security and privacy of their information.
Key Resources
Learn the Architecture: Realm Management Extension
Learn the Architecture: Introducing Arm Confidential Compute Architecture
Learn the Architecture: Arm Confidential Compute Architecture Software Stack
The Realm Management is documented in the Arm Architecture Reference Manual for A-profile.
Arm System Memory Management Unit Architecture Supplement
The Realm Management Extension (RME), for SMMUv3
Arm Architecture Reference Manual Supplement Memory System Resource Partitioning and Monitoring (MPAM), for A-Profile Architecture
Realm Management Monitor Specification
Arm Confidential Compute Architecture (CCA) Security Model (SM)
Get the videos from Arm CCA talks and panel session here.
Other Architectures
Find out more about our architectures.
The Arm CPU Architecture defines what a CPU must do when software runs on it.
Arm and its partners actively work to analyze and counter ever-evolving security threats.
Arm provides system architectures that are freely available to use and help the ecosystem design secure and efficient systems as easily as possible.